Moving-horizon false data injection attack design against cyber-physical systems
Abstract
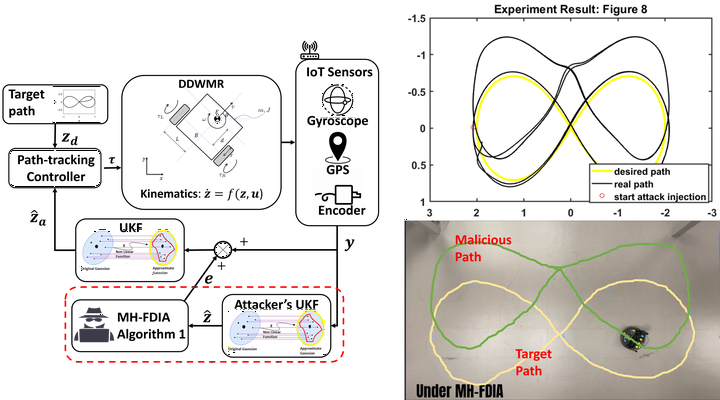
Systematic attack design is essential to understanding the vulnerabilities of cyber–physical systems (CPSs), to better design for resiliency. In particular, false data injection attacks (FDIAs) are well-known and have been shown to be capable of bypassing bad data detection (BDD) while causing targeted biases in resulting state estimates. However, their effectiveness against moving horizon estimators (MHE) is not well understood. In fact, this paper shows that conventional FDIAs are generally ineffective against MHE. One of the main reasons is that the moving window renders the static FDIA recursively infeasible. This paper proposes a new attack methodology, moving-horizon FDIA (MH-FDIA), by considering both the performance of historical attacks and the current system’s status. Theoretical guarantees for successful attack generation and recursive feasibility are given. Numerical simulations on the IEEE-14 bus system further validate the theoretical claims and show that the proposed MH-FDIA outperforms state-of-the-art counterparts in both stealthiness and effectiveness. In addition, an experiment on a path-tracking control system of an autonomous vehicle shows the feasibility of the MH-FDIA in real-world nonlinear systems.